💻 Configuration files to bootstrap a remote development box on GCP
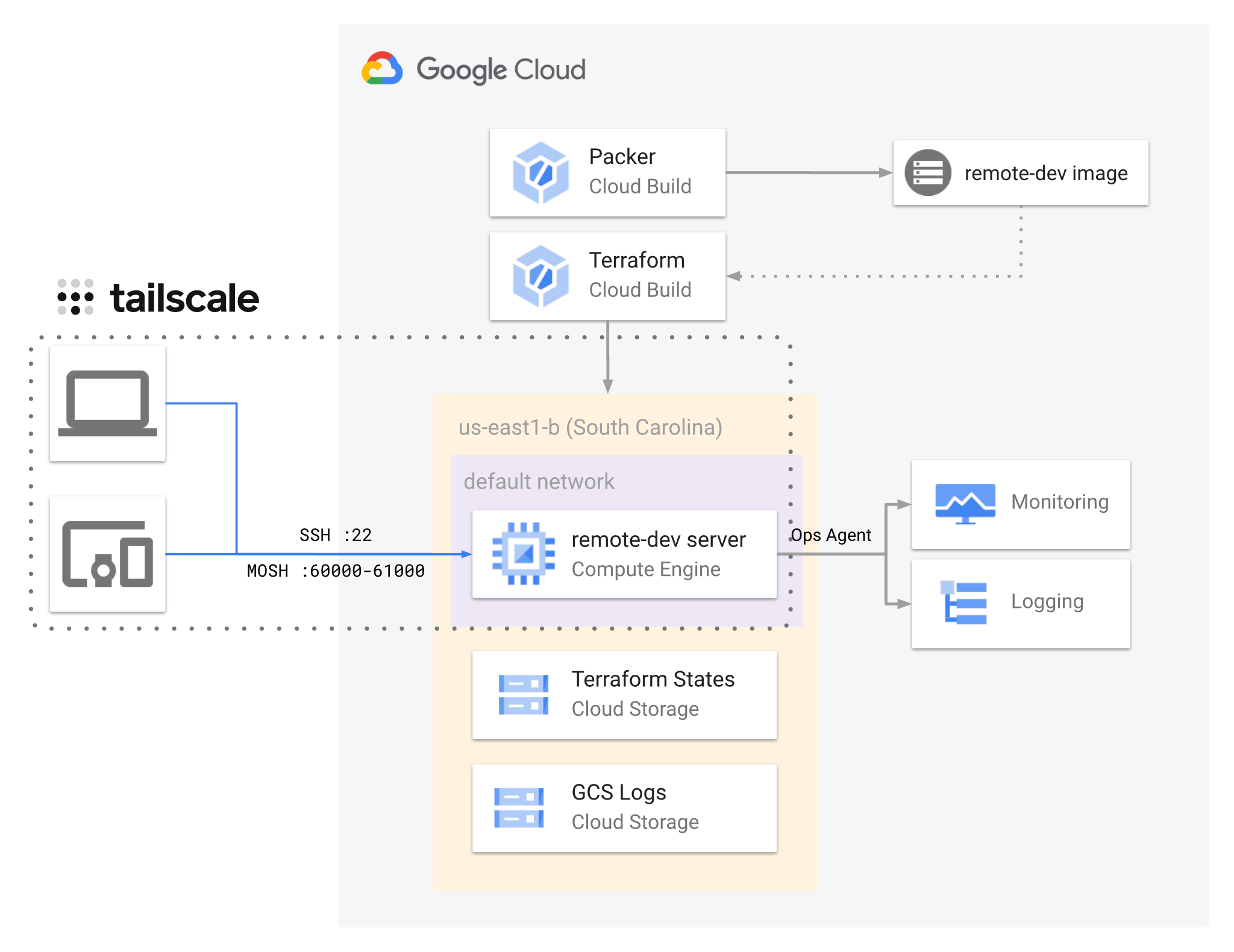
remote-dev (on GCP)Automate the provisioning of an ephemeral development server on Google Cloud Platform.
An immutable image is built with Packer and deployed on an e2-micro
Compute Engine instance (in us-east1-b to fall in the free tier) with
Terraform, all via Cloud Build.
The instance is only accessible via SSH and MOSH in your Tailscale network.
If you don’t have an SSH key pair already, generate one (preferably with a high-entropy passphrase):
ssh-keygen -o -a 100 -t ed25519 -C remote-dev
Run the setup script to set the permissions to call the services APIs and setup Packer/Terraform:
./run.sh -s
In the remote-dev repository, submit the Packer Cloud Build job:
./run.sh -p
In remote-dev/terraform/env/prod/terraform.tfvars, replace the SSH user/public key and Tailscale machines IP addresses
with your own values.
Generate a Tailscale ephemeral key and set it:
export TAILSCALE_KEY="tskey-xxx"
Then in the remote-dev repository, submit the Terraform Cloud Build jobs:
./run.sh -t
Once deployed, you can set explicit Tailscale ACLs like the following to
restrict network access in your mesh:
{"Hosts": {"remote-dev": "INSERT_IP_ADDRESS_HERE"},"ACLs": [{ "Action": "accept", "Users": ["INSERT_USERNAME_HERE"], "Ports": ["remote-dev:22,60000-61000"] }]}
In the remote-dev repository, submit the Terraform Destroy Cloud Build jobs:
./run.sh -d
This project is licensed under the MIT License - see the LICENSE file for details